
Hello friends , welcome back to hacking class, how to hack a website or website database today i will explain all the methods that are being used to hack a website or websites database. This is the first part of the class “How to hack a website or Websites database” and in this i will introduce all website hacking methods. Today I will give you the overview and in later classes we will discuss them one by one with practical examples. So guys get ready for first part of Hacking websites class…. Don’t worry i will also tell you how to protect your websites from these attacks and other methods like hardening of SQL and hardening of web servers and key knowledge about CHMOD rights that what thing should be give what rights…
Note : This post is only for Educational Purpose only.

What are basic things you should know before website hacking?
1. Basics of HTML, SQL, PHP.
2. Basic knowledge of Javascript.
3. Basic knowledge of servers that how servers work.
4. And most important expertize in removing traces otherwise u have to suffer consequences.
Now First two things you can learn from a very famous website for basics of Website design with basics of HTML,SQL,PHP and javascript. http://www.w3schools.com/
And for the fourth point that you should be expert in removing traces . For this you can refer to first 5 hacking classes and specially read these two…
1. Hiding Yourself from being traced.
2. Removing your Traces
As we know traces are very important. Please don’t ignore them otherwise you can be in big trouble for simply doing nothing. so please take care of this step.
METHODS OF HACKING WEBSITE:
1. SQL INJECTION
2. CROSS SITE SCRIPTING
3. REMOTE FILE INCLUSION
4. LOCAL FILE INCLUSION
5. DDOS ATTACK
6. EXPLOITING VULNERABILITY.
1. SQL INJECTION
First of all what is SQL injection? SQL injection is a type of security exploit or loophole in which a attacker “injects” SQL code through a web form or manipulate the URL’s based on SQL parameters. It exploits web applications that use client supplied SQL queries.
The primary form of SQL injection consists of direct insertion of code into user-input variables that are concatenated with SQL commands and executed. A less direct attack injects malicious code into strings that are destined for storage in a table or as metadata. When the stored strings are subsequently concatenated into a dynamic SQL command, the malicious code is executed.
For more basic knowledge about SQL injection visit:
The above tutorial consists of both types of SQL injection i.e. Manual and automatic through softwares. I will explain SQL injection in more detail with practical example in Next class.
2. CROSS SITE SCRIPTING
Cross site scripting (XSS) occurs when a user inputs malicious data into a website, which causes the application to do something it wasn’t intended to do. XSS attacks are very popular and some of the biggest websites have been affected by them including the FBI, CNN, Ebay, Apple, Microsft, and AOL.
Some website features commonly vulnerable to XSS attacks are:
• Search Engines
• Login Forms
• Comment Fields
Cross-site scripting holes are web application vulnerabilities that allow attackers to bypass client-side security mechanisms normally imposed on web content by modern browsers. By finding ways of injecting malicious scripts into web pages, an attacker can gain elevated access privileges to sensitive page content, session cookies, and a variety of other information maintained by the browser on behalf of the user. Cross-site scripting attacks are therefore a special case of code injection.
I will explain this in detail in later hacking classes. So keep reading..
3. REMOTE FILE INCLUSION
Remote file inclusion is the most often found vulnerability on the website.
Remote File Inclusion (RFI) occurs when a remote file, usually a shell (a graphical interface for browsing remote files and running your own code on a server), is included into a website which allows the hacker to execute server side commands as the current logged on user, and have access to files on the server. With this power the hacker can continue on to use local
exploits to escalate his privileges and take over the whole system.
RFI can lead to following serious things on website :
- Code execution on the web server
- Code execution on the client-side such as Javascript which can lead to other attacks such as cross site scripting (XSS).
- Denial of Service (DoS)
- Data Theft/Manipulation
4. LOCAL FILE INCLUSION
Local File Inclusion (LFI) is when you have the ability to browse through the server by means of directory transversal. One of the most common uses of LFI is to discover the /etc/passwd file. This file contains the user information of a Linux system. Hackers find sites vulnerable to LFI the same way I discussed for RFI’s.
Let’s say a hacker found a vulnerable site, www.target-site.com/index.php?p=about, by means of directory transversal he would try to browse to the /etc/passwd file:
www.target-site.com/index.php?p= ../../../../../../../etc/passwd
I will explain it in detail with practical websites example in latter sequential classes on Website Hacking.
HIRE VERIFIED DATABASE PENETRATION EXPERTS
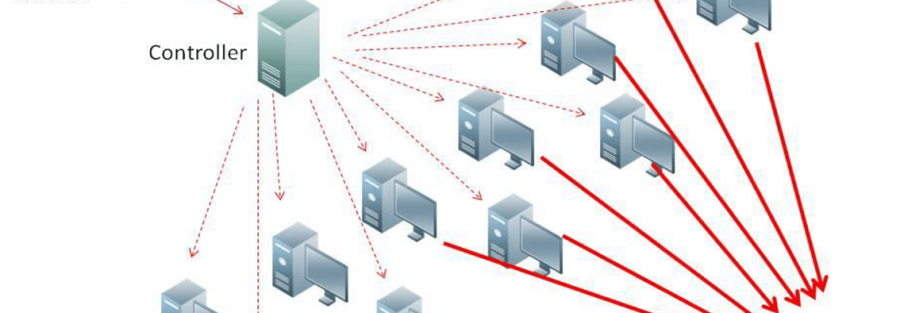
5. DDOS ATTACK
Simply called distributed denial of service attack. A denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) is an attempt to make a computer resource unavailable to its intended users. Although the means to carry out, motives for, and targets of a DoS attack may vary, it generally consists of the concerted efforts of a person or people to prevent an Internet site or service from functioning efficiently or at all, temporarily or indefinitely. In DDOS attack we consumes the bandwidth and resources of any website and make it unavailable to its legitimate users.

6.EXPLOITING VULNERABILITY
Its not a new category it comprises of above five categories but i mentioned it separately because there are several exploits which cannot be covered in the above five categories. So i will explain them individually with examples. The basic idea behind this is that find the vulnerability in the website and exploit it to get the admin or moderator privileges so that you can manipulate the things easily.
I hope you all now have a overview of that what is Website Hacking. In consecutive future classes i will explain all of these techniques in details. So guys keep reading..





9 Comments
LeStankeboog
there is a MASSIVE flaw in this suggestion. CTF’s are amazing to put what you have learned to the test… but CTF’s are not going to teach you core fundamentals. Every hacker should aspire to know not only the big picture but all the individual pieces that make up the puzzle. No CTF is going to help you memorize the 4 layers of the TCP/IP stack and the 7 layers of the OSI model. Not that knowing those two things are essential but a basic understanding of Networking (at least) ABSOLUTELY is. You could spend the next year playing with CTF’s everyday and only learn a quarter of what you could learn in a single CISCO networking course. I just feel that there is no substitution for really sitting down and studying the craft. Listen to a Defcon talk while you take a free Python class on CodeAcademy spend 30 minutes a day on a free class with Cybrary and another 30 minutes reading one of Kevin Mitnick’s book to help immerse yourself into the world and mindset of a hacker. I can only speak for myself but I had to break some bad, lazy habits. CyberSecurity saved my life and made me a better person. I feel like a part of that was making myself sit down and crack open a book for at least an hour a day, it helped create discipline. I got a hold of “The Basics of Hacking and Penetration Testing – by Pat Engebretson on Syngress Press.” By the time I finished it, I COULD NOT WAIT to restart it because I was getting apparent, noticable results. CTF’s are totally kickass, I endorse them fully (who the hell wouldn’t?!) but if learning is your goal I feel there’s faster ways to make gains. When it comes to practice though, there’s nothing on earth better than a CTF.
conscious source
I am thinking to give some time of life to hacking , besides math and physics as a other thing of my life, but how should I learn basics other than Linux , should I start at all , will I have enough time if I give 2-3 hours in weekends or more is needed? I Am full to full newbie but I like computers
Adam Weber
The short answer would be to start reading and install a Linux distro.
I personally do not recommend Kali linux, especially if you are installing it to hardware, BUT there’s a great no starch press book called ” Linux basics for hackers. It forces you to get involved in automating your system, learning terminal commands and writing some of your own tools and scripts. My only gripe is the author uses Kali Linux. It’s not typical of a Linux distro but it is THE pen testing distro. He installs it in virtual box. The book is very good for learning Linux in general as well. I would use that and skip most other books. Kali Linux revealed by the company who maintains Kali also is good.
I would also recommend getting a tcp/ip reference book. Might be pricey but I prefer print copies. Anything with computers needs reference material, especially when learning. It’s impossible to memorize everything but as your hand gets better at hacking you will remember the most common things.
Another book I would recommend is called “attacking network protocols” by James forshaw. If you read this, then compare what you’re confused with against a tcp/ip reference book, you will understand a lot more about what is going on.
This is why I was against using Kali, some people get tempted to use the tools right away but don’t understand how it works.
If I could start learning over and cut out the trial and error and confusion of information, I would do this.
greengobblin911
I myself was not a fan of the CTF approach and did the long term studying/theory approach.
I had a security class with who at the time seemed like the devil himself who liked CTFs and made use do them for labwork; it’s the “throw em in the water drown or swim” situation for learning hacking. It was a sentiment that teacher had and boy did I drown a lot.
I admire it for being the “quick and dirty” way to force you to learn a lot in a short amount of time, but I did not retain nearly as much as I would have if I had a better understanding of certain computer fundamentals related to OS features and Networking (TCP/IP). The CTFs forced me to know enough to pass the challenge, I wasn’t learning how to think or how to do research as if I was really building an attack vector or trying to come up with an exploit akin to what security researchers or some pen testers might do while under contract with a scope of devices that may be limited or obscure. Most of what I learned in his class I had to revisit to retain it despite the harsh introduction to those concepts CTFs provide.
I respect OP’s post whole-hardheartedly considering I have not seen a post assembled so well as he did it, but there’s a certain “discipline” i think you find in having to comb through the boring stuff including the fundamentals that will make CTFs easier and more exciting when the person doing it understands what they’re doing. As others said, CTFs vary so much; if someone does not diversify themselves in their CTFs they would fall into a niche or one type of hacking. Its not necessarily bad, but I feel like it limits your prospects.
Sometimes the boring theory over a period of time builds a bank of knowledge where you can know where to look for certain things despite the limited basic knowledge. Like that scary professor used to tell me:
“information security is a mile wide and an inch deep”
you have to know a little bit of everything to start, not necessarily have the outcome ready and at hand. That does come with the practice of multiple CTFs, but my concern is someone who finds they are good at say, website pen-testing based CTFs, might only continue this because they find the gratification in solving the challenges,and being right all the time, especially for new and younger individuals, not everyone likes to hack because they like computers or are nerds like you say, movies and the media made people like us for better or worse, the “hip and cool” guys to be right now. They would lack that “shallow ocean” of starting material to even consider trying their hand at something else like memory analysis or reverse engineering. I think that would start to bite you in the butt if they start to do this (hacking and penetration testing) professionally.
Take someone like Samy Kamkar for instance: Starts off as a Programming prodigy, makes his own company and inadvertently creates a XSS javascript worm and gives him notoriety. Starts off with just web based stuff. Regardless if you like the guy or not, he’s a critical thinker; since then he’s had a variety of projects and attacks with a whole breath of varied technologies from NFC to PHP backends or RFID. His most recent stuff involved applied and time tested network attacks like MITM to smart/connected cars.
What no one likes to acknowledge (or think about I should say) is the man like many other hackers and researchers comb over books and documentation and have to read and do “boring” research which might mean not being in front of a computer all the time. Hardware hacking is like a complete 360 from what he started off with, and certain exploits such as a MITM on a car comes from understanding of fundamentals and implementing it creatively. You wouldn’t piece together different things like he would unless you understood the basics very well and was creative and experimented. The guy isn’t a mastermind by any stretch, but he’s one of those researchers that takes the wide limited knowledge approach and then forms a scope for further investigation and research. A CTF has an answer to it that is known to someone else, it may not be the best way to encourage creative thinking for the real application of hacking skills.
Note However, Capture the Flags could form a gratification loop in new inexperienced hackers as compared to forcing newbies to learn a little bit about everything including the fundamentals, as the gratification/feedback loop they enter keeps them focused on CTFs they are “good” at and limits their prospects in other areas of hacking they may have not considered because they don’t do research on CTF topics they are not good at. This limits the ability to think of creative solutions (like those needed for real world exploit development/hacking).
Nathan Morwood
Thanks for the great post.
Question: where’s the 1 place to start IYHO if you know nothing at all and want a focus / career in cyber security and practical application pentesting for personal SHTF prep.
I have about 5 mins of script kiddo experience.
I’m hardcore into learning Linux and command terminal via Mint for past month.
I’ve made hello world a few times and have forgotten since.
Seems a skill easier to learn in a group. I Def don’t have a mentor or any cool kids to hack with all day.
billy C Crawford
My problem with CTF as a method of “learning to hack” is that all of the steps you take are in service of finding a flag, and the timing aspect makes it less likely that what you are doing is going to end up in your long-term memory. For some individuals, like me, it can be kind of a poor substitute for learning. I definitely need to take some time to really learn the basics and get comfortable with linux and networking before I go back to attempting CTFs. For me, sitting down with books and tutorial videos is a good method, at least for where I am at right now. So I definitely agree with you in that regard
vaughn Sebastien
I do understand what you are saying here, but I have to disagree with you on the point of not ‘knowing the fundamentals’. CTF naturally forces you to learn the fundamentals in a very intense manner. There is no way you can progress through a CTF without understanding the ‘big picture’, and it most definitely does not teach you how to do very specific things in very specific situations.
Take for example a simple case of any binary exploitation challenge – it requires you to disassemble the program in order to analyse the machine code – so that you can map out each and every individual function. You then use what you see to build a mental image of what you’re dealing with, and then finally at that point do you consider your options for exploitation. In a matter of a few steps we’ve already covered learning the use unix commands, how a program is assembled in machine code, how to read the machine code itself, how the machine code interacts with the system’s memory, and how to reverse-engineer such machine code into it’s respective high-level language functions. Understand that CTF requires you to know the fundamentals/’big picture’ as fluently as possible before you could even progress through the simplest of challenges.
This example only covers one case, as CTF also expands out into forensics (stenography, data, & analysing network packets), web exploitation (which forces you to learn everything from js, html, php, common libraries, API’s, to full stack web development), miscellaneous (which involves crucial scripting skills) and cryptography (for mathematics & encryption). In each and every single case you must understand fully what you are dealing with, or else you would be left lost with no direction.
Through this knowledge alone one would eventually start seeing the intricacies of technology around us, and thus begin to see how they can apply their knowledge for use in real-world situations. The point of CTF may be directed towards exploitation, but there is any underlying set of fundamentals you must learn & apply if you want any chance of success – and this learned knowledge alone should be more than enough to use in real world scenarios.
vermin berahinho
I suppose it depends on how you look at it.
On one hand, CTFs do work as you’ve explained here, however because CTFs have a myriad of categories and challenges, you really end up putting yourself in specific situations for each challenge and then moving onto a completely separate situation and possibly forgetting the previous challenge.
Working your way up through the fundamentals and then focusing on one aspect of InfoSec (binex, netsec, websec, etc) for a long time until you truly understand it, then moving onto another category allows you to build your understanding without drinking from the firehose of security by taking multiple categories of challenges at one time.
Of course, CTFs/wargames are a great supplement for this type of learning. For example, if you are working on reverse engineering, smashthestack would be great to supplement readings of that type of subject to get practical experience.
Of course, this is just my opinion from my experience in the field. In obtaining the OSCP/OSCE and real-world pentesting, I’ve found that building the fundamentals separately helps much more when turning them into security related concepts and as hard as it might be to figure out and backtest, ill rather you hire experts to help you although it might come expensively.
gabriel aliday
Data breaches are a common occurrence in today’s world and the consequences can be devastating. In this article, we look at how hackers can breach a database, what the consequences are, and what you can do to protect your information.
Data breaches are one of the biggest threats that companies face today. They put customer data at risk, as well as company secrets and intellectual property. If you’re a company owner or manager, it’s important to know how hackers get in so that you can be aware of any threats that your company might face.
There are two types of data breaches: external and internal. External attacks usually involve social engineering or hacking – accessing a third-party service like Facebook to get into an account on another site where they don’t have access. Internal attacks happen when someone within