How To Hack Database with SQL
How to hack database with SQL is not childs play as one is going to have to get to really understand the query language of the database you are targeting. You are going to have understand:
- data return, modification and addition methods
- How the different types of joins work and when they can be used. How to handle many to many joins
- Structure that the data is returned in and how to parse it
- common encryption methods. Note if it is done properly it can be near impossible to read any of the data.
- Webform security. Most webforms use filters specifically to block database queries, so you will also need to understand the front-end language used to filter the form, like javascript
While there are a multitude of different types of hackers, the database is the one goal they all share. I refer to the database sometimes as the Holy Grail of the hacker, or the ultimate reward for an efficient hack.
That is because the database is the repository of all the goodies that the hacker is after, almost by definition. Credit card records, personally identifiable information, usernames and passwords, and intellectual property may be included in these goodies.
For instance, credit card numbers can be sold for between $5 to $50 depending upon the quality (gold and platinum cards are worth more than regular cards) and their credit limit. So, a hack that reaps 200,000 credit cards numbers is worth anywhere from $1 to $10 million!

How To Hack Database with SQL
At the same time, hackers funded by the state, such as China, are after intellectual property. This will include designs, formulas, engineering, and other items which Chinese companies would steal and carry to China for manufacturing. This happens every day and some consider it to be the biggest fraud in the world’s history!
This is the first installment of a new null-byte series on database hacking. Before we examine how to hack a database, we need to understand the basics of how databases work, what SQL is, and what vulnerabilities are common to databases.
So, let’s get started so that we can quickly get to some DB hacking!
What Is a Database?
A database is a system of software to store and retrieve information in a structured format. Early databases were flat files, kind of like a big Excel file. As databases got bigger and bigger, this simple structure proved inefficient.
hence,
As a result, a scientist at IBM, Dr. Codd, developed a structure that came to be known as the relational database model. It is this model that about 97% of all databases now use, and this includes all the major software companies.
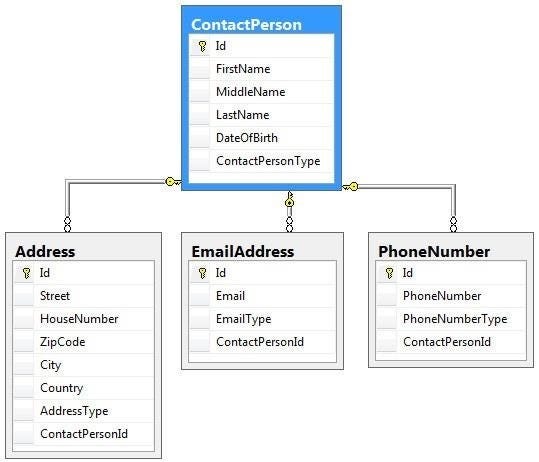
The basics of the relational model is that data should be placed in separate tables with unique keys that link the tables to avoid data duplication and to ease the retrieval of this data.
By using a shared column or ‘key’, this relational database model connects data from different tables. The diagram below is of a basic relational database model where the column ‘ID’ connects all the tables.
How To Hack Database with SQL
There are several vendors in the enterprise database market selling products that can perform the same role, but in different ways. In this market, the major players are:
- Oracle. They are the behemoth in this market with nearly 50% market share. They own multiple different database software products, including their namesake and MySQL.
- Microsoft SQL Server. Microsoft entered this market in the early ’90s by teaming up with Sybase to develop an enterprise database offering. As a result, MS SQL Server and Sybase still share many similarities. Originally, Microsoft was only a player in the small business market, but is slowly gaining traction in the larger enterprise market.
- MySQL. This is an open-source database that you will find behind so many web sites, in part, because it’s free.
- IBM DB2. IBM was the original enterprise database provider and made many the major developments in database design, but like everything about IBM, it has been in decline in recent decades.
Other major vendors include Sybase, SAS, PostgreSQL (open source), and many others. Generally, like any hack, we need to do good recon to determine the software and version to be successful as most of the database hacks are vendor specific.
Structured Query Language (SQL)
When IBM developed the early databases, they also developed a programming language for managing and manipulation this data. They called it “Structured Query Language,” or as it is generally known, SQL.
This is a simple language that uses English words in similar ways that humans who speak English use them. For instance…
SELECT means “select some data from columns in a table”
FROM means “get the data from this table”
WHERE means select the data that meets this condition (lastname = ‘smith’).
Furthermore, words such as UPDATE, INSERT, and DROP mean in SQL exactly what you would expect them to mean.
SQL is not picky about syntax, but it is picky about logic. Although best practice is to CAPITALIZE all keywords (SELECT, FROM, WHERE), it’s not required. In addition, white space is ignored. All but Microsoft, though, require that a SQL statement to end in a semicolon (;). On Microsoft products, it’s optional.
SQL is standardized by ANSI, but this standardization only includes about 80% of the language or the core of SQL. Software publishers are free to add additional commands and features that are not part of the standard. This can sometimes make it difficult to transport SQL code between DBMS. It also makes it critical to do good reconnaissance on the database to know the manufacturer and the version before attacking as the attacks are often specific to the manufacturer and the version.
Each of the DBMS can be used from a command line, but each has its own GUI. Recently, MySQL released a new GUI called Workbench as seen in the previous section.
Oracle, Microsoft, and the others have similar GUIs that allow the administrator to access their systems.
Basic SQL Query
When we need to extract data from the database, it’s said that we are “querying” the database. As databases are repositories for data, the ability to extract or query data is among the most important functions. As a hacker, we want to extract data, so the query is critical to getting the goods.
The basic structure of the query looks like this:
SELECT <columns>
FROM <table>
WHERE <conditions>
This statement says “give me the data in the columns listed in the SELECT statement from the table that comes after the FROM keyword but only give me the rows that meet the conditions that come after the WHERE keyword.”
So, if we wanted to get first name, last name, username, and password from the staff table for employees with the last name of “Hillyer,” we could construct a statement like this:
SELECT first_name, last_name, username, password FROM staff WHERE last_name = 'Hillyer"; How To Hack Database with SQL
As you can see in the screenshot above, we have extracted Mike Hillyer’s record from the staff table with his username and password (the password is actually a hash of his password).
SQL Injection
SQL injection is the most common database attack and is probably responsible for the largest dollar volume of losses from cyber crime and advanced persistent threat (APT).
It basically involves putting SQL commands in the data forms of webpages that connect to a database. These forms then send these SQL commands back to the database and the database will either authenticate the user (yes, authentication is a database function) or give up the target data.
In future tutorials, we will spend quite a bit of time using SQL injection tools and executing SQL injection attacks.
Other Vulnerabilities
Besides showing you how to do SQL injection, we will examine some of the other of vulnerabilities in databases. These involve authentication, using the database to compromising the operating system, and several others.
Now that we having covered the basic terminology and technology related to databases, in future tutorials I will show you how to hack into these databases, so keep coming back!
Want to start making money as a white hat hacker? Jump-start your hacking career with our 2020 Premium Ethical Hacking Certification Training Bundle from the new Null Byte Shop and get over 60 hours of training from cybersecurity
.





5 Comments
Travisky
Contact @h4ckerspro on Telegram hacker he is reliable in any kind of hacking job, am so much happy working with him because he regained access to my lost Email, He helped me hack into a bitcoin site and recovered my lost $127,000 Dollars, and also hacked into husband’s phone without him getting any notice or alarm, Honestly he is very great in hacking jobs, I can strongly recommend to contact him for help, he is trustable.
Letizia Trentini
When I was in college, it was really hard to manage my grades. I wanted to keep up a good GPA but sometimes had trouble with the workload. So, I contacted TheHackerspro and they told me all about their hack school database. they get to penetrate the school database and change your grades. They have helped me immensely.
Fiorello Lorenzo
I am a computer expert and I have been looking for the best hacking firm outhere as most of the ones i have hired on youtube have ended up not doing my job. i needed to penetrate into a rival website so as to have it shut down for some hours. i hired vladimir kolarov and he brought it down for 3 days. crazy dude… lol. i was so amazed at their expertise. After tons of research, I found this one to be the most reliable and easy to use. It’s so simple! The interface is really neat and super helpful. The best part is that their customer support is always live and available
Orlando Rizzo
First I want to say that I am glad I found TheHackerspro and their service. The platform is straightforward and easy to use, even for those who are a bit tech-averse. They offer clear pricing models, profiles of all their experts, as well as video tutorials. You know exactly what you’re getting before you even sign up!
lizzy Lager
To protect their data, companies need to invest in cybersecurity. However, they also need to be able to stop hackers from accessing their servers.
Hackers have been using various methods to hack databases for decades and they are constantly creating new strategies and finding new ways of exploiting the weaknesses in database security. To protect a company’s database, it is vital that companies take all possible precautionary measures and create a system that can stop hackers in their tracks.
Some preventive measures that are helpful include:
-making sure that all employees know what social engineering techniques are and how to spot them;
-keeping your system updated with the latest patches;
-having strong passwords;
-using an SSL certificate;
-installing a firewall;
-using anti malware programs