
How to hire hackers This article is an update on how to hire hackers, as the world of hacking has changed a lot in recent years.
The hacker’s toolkit is a list of tools that hackers use to carry out their attacks. It includes everything from network scanners to packet sniffers and password crackers. If you want to be a hacker, you need to understand how these tools work and what they do before deciding to hire hackers for your penetration or phone hacking.
A hacker’s toolkit is a set of software, hardware, and other tools used by computer hackers to break into computer systems.

The hacker’s toolkit is constantly evolving. It has evolved in the past years from just a laptop and some software to an extensive collection of software and hardware that can be carried in a backpack. The change in the hacking tools’ size is due to its portability.
How to hire hackers
As with any other profession, hackers have their own set of tools that they use for their work. These are not just limited to computers; they also include things like lock picking kits, screwdrivers, etc.
The hacker’s toolkit is a set of tools that are used by hackers to break into computer systems.
The hacker’s toolkit is an essential part of the cyber security world. It includes a variety of tools and software that can be used to hack into computer systems. All in all, the tools that are in this kit will help you figure out how to break into a system and what measures you need to take in order to protect it.
The hacker’s toolkit has been updated since its inception, with new technology being added as time progresses. The new version includes more sophisticated hacking techniques, such as those used by professional hackers who work for the government or private companies
We thought that this would be a good time to update this popular article, as new tools to hack private communications in WiFi hotspots are always evolving. This article discusses some of the most well-known WiFi hacking tools.

Instructions
Unfortunately, rookie hackers don’t have to look far to learn what they need to know about hacking.
Kali Linux, for example, is one of the most well-known hacking tool sets, and its website has numerous how-to hacking links.
More than 300,000 videos on WiFi hacking have been uploaded on YouTube, with some garnering millions of views.
Hackers Tools Kit & how to hire hackers
“How to hack any WiFi hotspot in around 30 seconds” is one of the first items on the list.
There are many additional hacking websites out there, but we don’t want to link to them because many of them are suspect and may include viruses.
Hackers are a common sight in the news, and many people are worried about their security. However, there is a way to get hackers to protect you: hire them for penetration testing.
Penetration testing is a method of evaluating the security of an information system by simulating an attack on it. It usually involves professionals who use software and other tools to find vulnerabilities that can be exploited by hackers.
This type of testing has been around for decades but it became popular after the 9/11 attacks. The US government realized that they needed to evaluate their systems more thoroughly and hired outside experts hackers to do so.
As time went on, more companies started using this type of testing because it was cheaper than hiring additional IT staff or buying new equipment for their IT departments.
Thus Hacking is the process of exploiting computer systems and networks to achieve a desired system goal, usually without authorization.

Hacking is the process of exploiting computer systems and networks to achieve a desired system goal, usually without authorization. Penetration testing is an active measure taken by organizations to assess their level of security and identify their vulnerabilities. It involves the use of specialized tools and techniques that are designed to simulate an attack on the company’s network, with the intention of finding security weaknesses before a malicious individual does. it is usually subcontracted to Ethical hackers and that is why a lot of companies are always looking for how to hire hackers
How to hire hackers
Many companies hire hackers for penetration testing because it helps them identify vulnerabilities in their systems before they are exploited by malicious individuals. How to hire hackers would be the most song rendered on their lips
Hackers are not just a group of people who break into computers and steal information. They can also be the ones who help businesses with their security needs. This is where hiring a hacker for penetration testing comes in handy. Penetration testers are hackers hired to test the security of an organization’s network and computer systems, looking for vulnerabilities that could be exploited by malicious hackers.
Penetration testing is a very important step in securing your business and data from malicious hackers.

Software
The following are the top 10 tools preferred by both ethical and black hat hackers in 2022:
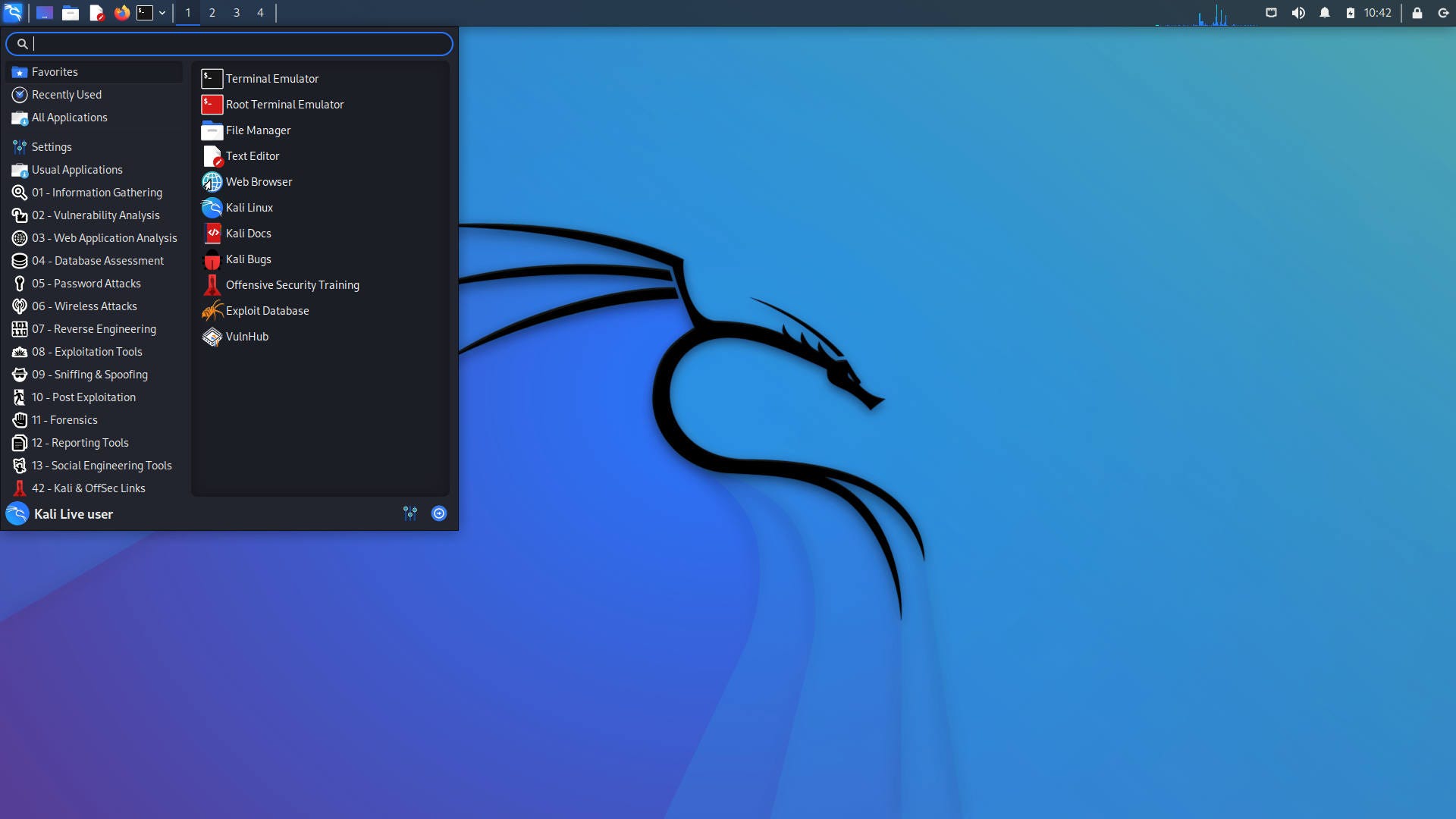
- Kali Linux: Kali Linux is a Debian-based distribution designed for digital forensics and penetration testing. It comes with more than 600 open source hacking tools pre-installed for the various tasks.
Over 600 penetration-testing apps are preloaded on Kali Linux, including nmap (a port scanner), Wireshark (a packet analyser), John the Ripper (a password cracker), Aircrack-ng (a software package for wireless LAN penetration testing), Burp suite, and OWASP ZAP (both web application security scanners). Kali Linux can be installed on a computer’s hard disk and run natively, or it can be launched from a live CD or USB and run in a virtual machine. It is a supported platform for the Metasploit Framework, a tool for designing and executing security exploits developed by the Metasploit Project.
It was created by TheHackerspro Security’s Expert Vladimir Kolarov and Devon Kearns as a rebuild of BackTrack, their prior forensics Linux version based on Ubuntu.
Raphael Hertzog, the third core developer, joined them as a Debian expert.
Kali Linux is based on the Debian Wheezy distribution.
The majority of the packages Kali utilises come from the Debian repositories.
Kali Linux is created in a secure environment, with only a small number of trustworthy individuals permitted to commit packages, each of which is signed by the developer.
Kali also contains a modified kernel that has been patched to allow for injection.
This was added mostly because the development team discovered that they needed to do numerous wireless assessments.
2. Metasploit: Metasploit is a software that helps people to find and exploit security vulnerabilities in applications, operating systems, networks, hardware devices etc.
3. Wireshark: It’s a network protocol analyzer tool used to capture data packets on a network or internet connection, so as to examine them later on.
White hats and DevSec experts can use pen-testing tools to probe networks and applications for flaws and vulnerabilities at any step during the production and deployment process.
The Metasploit Project is one such penetration testing tool. This Ruby-based open-source framework provides for command-line or GUI-based testing.
It can also be repurposed as an add-on that supports multiple languages through code.
The Metasploit is a complex tool that may be used to analyse network and server vulnerabilities by both criminals and ethical hackers. Because it’s an open-source framework, it’s simple to customise and adapt to most operating systems.
Metasploit can be used by a pen testing team to inject ready-made or bespoke code into a network in order to find vulnerabilities. Once issues have been identified and documented, the information can be used to address systemic flaws and prioritise solutions, which is another type of threat hunting.
4. Nmap: Nmap or Network Mapper is an open source tool for network exploration or security auditing. Network administrators utilize this hacking tool for security and auditing objectives. It uses IP packets to figure out what hosts are on the network, what services they provide, what protocols are in use, what OS systems are on the network, and what kind of packet filters and firewalls are in use.
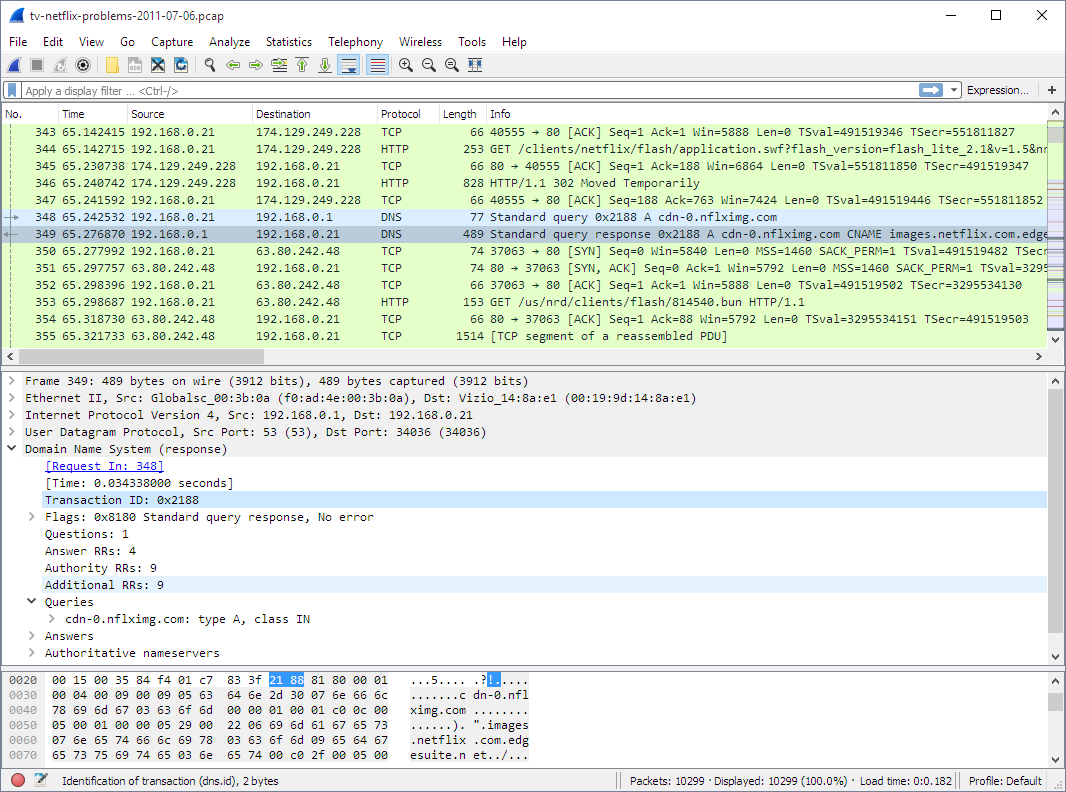
5. Wireshark is the world’s foremost and widely-used network protocol analyzer. It lets you see what’s happening on your network at a microscopic level and is the de facto (and often de jure) standard across many commercial and non-profit enterprises, government agencies, and educational institutions. Wireshark development thrives thanks to the volunteer contributions of networking experts around the globe and is the continuation of a project started by Gerald Combs in 1998.
Hackers Tools Kit & how to hire hackers
Wireshark has a rich feature set which includes the following:
- Deep inspection of hundreds of protocols, with more being added all the time
- Live capture and offline analysis
- Standard three-pane packet browser
- Multi-platform: Runs on Windows, Linux, macOS, Solaris, FreeBSD, NetBSD, and many others
- Captured network data can be browsed via a GUI, or via the TTY-mode TShark utility
- The most powerful display filters in the industry
- Rich VoIP analysis
- Read/write many different capture file formats: tcpdump (libpcap), Pcap NG, Catapult DCT2000, Cisco Secure IDS iplog, Microsoft Network Monitor, Network General Sniffer® (compressed and uncompressed), Sniffer® Pro, and NetXray®, Network Instruments Observer, NetScreen snoop, Novell LANalyzer, RADCOM WAN/LAN Analyzer, Shomiti/Finisar Surveyor, Tektronix K12xx, Visual Networks Visual UpTime, WildPackets EtherPeek/TokenPeek/AiroPeek, and many others
- Capture files compressed with gzip can be decompressed on the fly
- Live data can be read from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others (depending on your platform)
- Decryption support for many protocols, including IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP, and WPA/WPA2
- Coloring rules can be applied to the packet list for quick, intuitive analysis
- Output can be exported to XML, PostScript®, CSV, or plain text
6. SQLMap
Sqlmap is an open source penetration testing tool that automates the process of discovering and exploiting SQL injection problems as well as database server takeover.
It includes a robust detection engine, numerous specialist features for the ultimate penetration tester, and a wide range of switches that span database fingerprinting, data retrieval from databases, access to the underlying file system, and out-of-band command execution on the operating system.
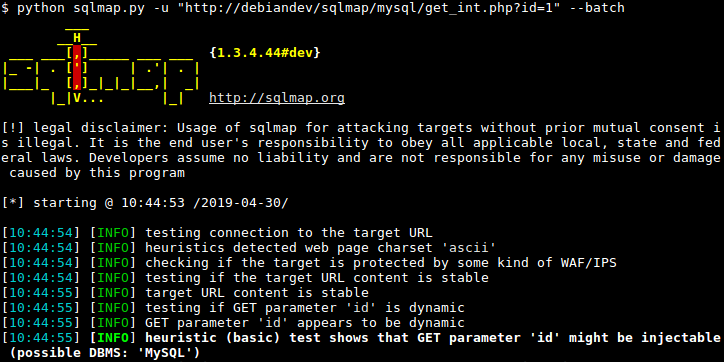
Features
- Full support for MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, Informix, MariaDB, MemSQL, TiDB, CockroachDB, HSQLDB, H2, MonetDB, Apache Derby, Amazon Redshift, Vertica, Mckoi, Presto, Altibase, MimerSQL, CrateDB, Greenplum, Drizzle, Apache Ignite, Cubrid, InterSystems Cache, IRIS, eXtremeDB, FrontBase, Raima Database Manager, YugabyteDB and Virtuoso database management systems.
- Full support for six SQL injection techniques: boolean-based blind, time-based blind, error-based, UNION query-based, stacked queries and out-of-band.
- Support to directly connect to the database without passing via a SQL injection, by providing DBMS credentials, IP address, port and database name.
- Support to enumerate users, password hashes, privileges, roles, databases, tables and columns.
- Automatic recognition of password hash formats and support for cracking them using a dictionary-based attack.
- Support to dump database tables entirely, a range of entries or specific columns as per user’s choice. The user can also choose to dump only a range of characters from each column’s entry.
- Support to search for specific database names, specific tables across all databases or specific columns across all databases’ tables. This is useful, for instance, to identify tables containing custom application credentials where relevant columns’ names contain string like name and pass.
- Support to download and upload any file from the database server underlying file system when the database software is MySQL, PostgreSQL or Microsoft SQL Server.
- Support to execute arbitrary commands and retrieve their standard output on the database server underlying operating system when the database software is MySQL, PostgreSQL or Microsoft SQL Server.
- Support to establish an out-of-band stateful TCP connection between the attacker machine and the database server underlying operating system. This channel can be an interactive command prompt, a Meterpreter session or a graphical user interface (VNC) session as per user’s choice.
- Support for database process’ user privilege escalation via Metasploit’s Meterpreter
getsystemcommand.
8. Cain & Able:This is a multi-purpose programme that can intercept network traffic and use the information contained in those packets to crack encrypted passwords using dictionary, brute-force, and cryptanalysis attack methods, record VoIP calls, recover wireless network keys, and analyse routeing protocols. Its primary goal is to make password and credential recovery easier. Over 400,000 people have downloaded this programme.
The rest are
Burp Suite, Maltego CE (Community Edition), Aircrack-ng suite
Hackers are the most important and influential people in the world. They are responsible for the safety of our data, our privacy, and our security. As such, it is essential to know what tools they use to achieve their goals.
In order to protect ourselves from hackers we must first understand them and their methods.
Ethical hackers, also known as white-hat hackers, use a variety of hacking tools to identify vulnerabilities in the system and fix them. Black hat hackers, on the other hand, use these tools to exploit vulnerabilities and take advantage of them.
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 |





2 Comments
Amy Shaul
My mom and I bear the same name and her credit information gets put on my credit report a lot. It became a struggle for me and I felt like I was living in someone else’s shadow. When things weren’t paid or went into collection or judgment my credit took a hit so I needed them to make the correction, restore my credit and make it stop. No one could help until vladmir of thehackerspro Steeped in and corrected the mistake, restored my credit to high 750s and put a permanent stop to the constant report of my mom’s credit info on my credit report.now we are able to get a loan on our mortgage to purchase a property here in silicon valley
Susie
You can see everything on your spouse phone by getting it hacked, that’s what i did for ex- husband when i noticed he’s been cheating on me i just have access to his phone remotely thanks to the best hacker i know thehackerspro.com they are a genius reliable, considerate and affordable they can also help you with retrieving lost data, lost/hacked social media, recover stolen or scammed crypto even Blockchain protection. they can also help you protect your phone from been hacked . They are the best for the job you can reach him through Email – Or theh4ckerspro on Instagram